
OT Security Best Practices Checklist
This checklist highlights best practices for ensuring the security of your organization’s OT environment. Based on the Purdue Reference Model for industrial control network segmentation, this checklist defines the layers, components, and boundary controls for securing these networks.
We suggest using this checklist as a guide and not a complete set of steps for securing every type of OT environment.
Follow the Perdue Reference Model
- Ensure IT assets are separated from OT assets using a formal network topology (see chart).
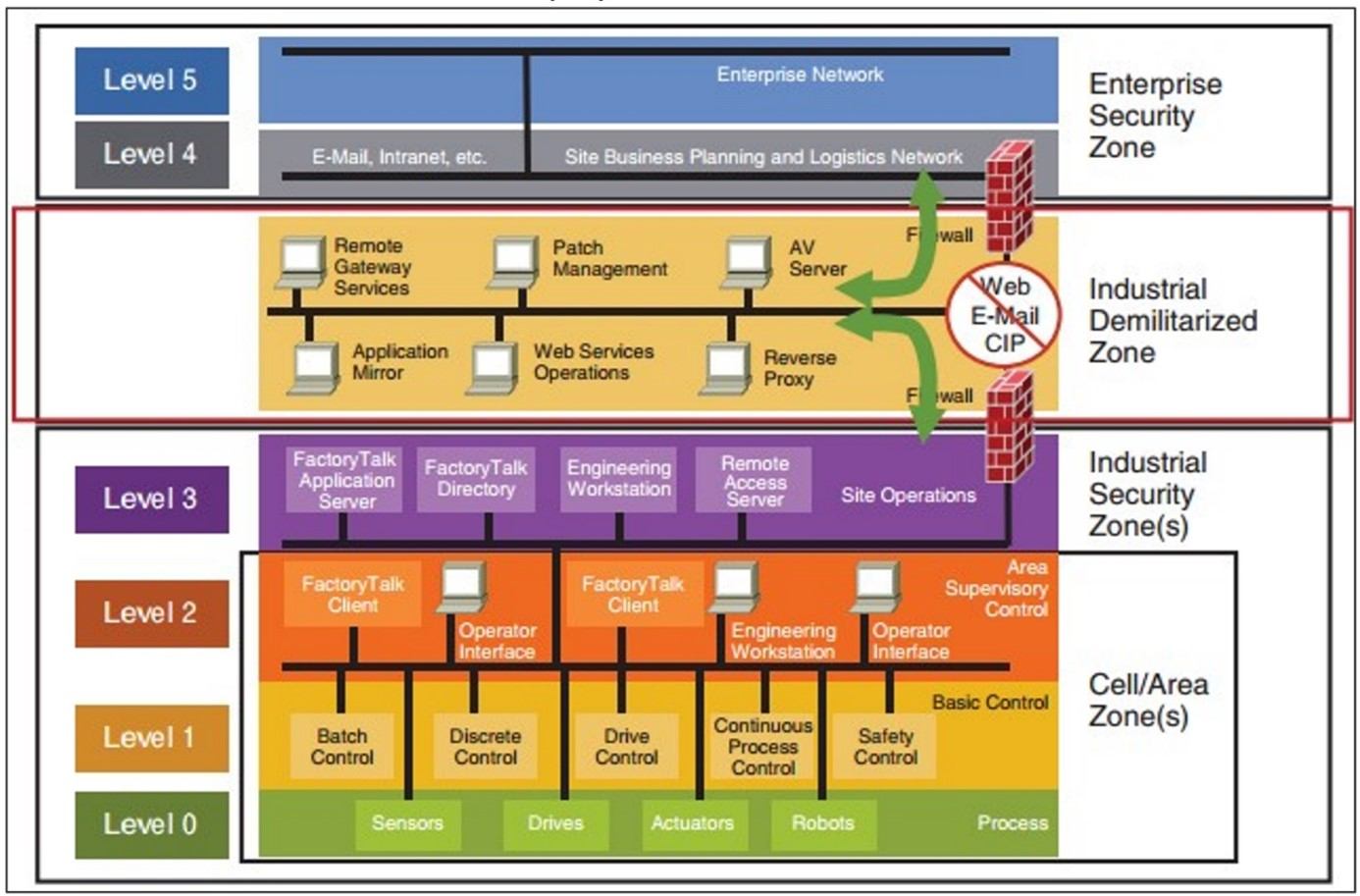
- Ensure network security controls prevent users in the Industrial Security Zone from accessing arbitrary destinations on the internet.
- Ensure network security controls prevent users in the Industrial Security Zone from accessing arbitrary destinations in the Enterprise Security Zone.
- Ensure network security controls prevent users in the Cell/Area Zones from accessing arbitrary destinations on the internet.
- Ensure network security controls prevent users in the Cell/Area Zones from accessing arbitrary destinations in the enterprise security zone.
- Consider the risk level of all approved communications/destinations. For example:
- Communications from the Industrial Security Zone to the Enterprise Security Zone are high risk.
- Communications from the Industrial Zone to the internet are higher risk.
- Communications from the Cell/Area Zones to the enterprise security zone are even higher risk.
- Communications from the Cell/Area Zones to the internet are the highest risk.
- Ensure all such communications are documented with the following:
- Business/process owner
- Description and justification for the destination
- Security approver
- Date of implementation
- Date of next scheduled review
- Ensure communications among devices within Cell/Area Zones are limited to only those necessary for operations.
Deploy an IT/OT Segmentation Method:
- Choose among airgap, firewall and data diode.
- If your organization uses another segmentation method (e.g., cross-domain solution), pick the closest solution and modify where applicable.
READ: 7 Steps to Align IT, OT and Physical Security
Ensure Airgap Segmentation is Secure:
- Have a red team evaluate whether the solution is truly air-gapped from the IT side of the network airgap.
- Have a red team evaluate whether the solution is truly air-gapped from the OT side of the network airgap.
- Define a process for transferring system updates to the OT side of the network airgap.
- Ensure the process is regularly followed (e.g., patching being performed at least every 90 days).
- Define a process for transferring OT telemetry to the IT side of the network airgap.
- Define a process for identifying security alarms that occur on the OT side of the network airgap.
READ: Understand the Roles of Red, Blue and Purple Teams
Ensure Firewall Segmentation is Secure:
- Have a red team evaluate whether the firewall is the only method by which data can be moved from the IT side of the network to the OT side of the network.
- Have a red team evaluate whether the firewall (as configured) appropriately limits lateral movement from the IT side of the network.
- Have a red team evaluate whether the firewall (as configured) appropriately allows OT telemetry to be transferred (as required) from the OT side of the network.
- Define a process for transferring system updates to the OT side of the firewall.
- Ensure the process adequately limits lateral movement risk (in most cases, Server Message Block shares have unacceptable residual risk).
- Ensure the process is regularly followed (e.g., patching being performed at least every 90 days).
- Ensure the firewall solution is configured so security alarms that occur on the OT side of the network are visible on the IT side of the network.
- Put an audit process in place to regularly review the logs from the firewall solution and identify any misuse of the IT-to-OT network connection.
Ensure Data Diode Segmentation is Secure:
- Have a red team evaluate whether the data diode is the only method by which data can be moved from the IT side of the network to the OT side of the network.
- Have a red team evaluate whether the data diode (as configured) limits transfer of data from the IT side of the network to the OT side of the network.
- Ensure only specifically configured file types (such as software updates) are allowed.
- Have a red team evaluate whether the data diode (as configured) appropriately allows only specific file types (including OT telemetry) to be transferred (as required) from the OT side of the network.
- Define a process for transferring system updates through the data diode.
- Ensure that process is regularly followed (e.g., patching being performed at least every 90 days).
- Ensure the data diode is configured so security alarms that occur on the OT side of the network will be visible on the IT side of the network.
- Put an audit process in place to regularly review the logs from the data diode to identify any misuse of the IT-to-OT network connection.
Deploy OT Network Modeling Controls:
- Realize most controls are not binary and have various levels of efficacy, depending on the deployment model.
- Ensure east-west NetFlow is logged in the OT network.
- Ensure east-west enhanced network metadata (e.g., from Zeek/Bro) is logged in the OT network.
- Ensure network monitoring logs are retained long enough to provide useful artifacts for investigative requirements.
- Ensure human-machine interfaces and other Windows-based or Linux-based end-user systems run antivirus, endpoint detection and response, or other endpoint security tools.
- Ensure security tools on Windows-based or Linux-based end-user systems on the OT network are regularly updated.
- Ensure security tools on Windows-based or Linux-based end-user systems on the OT network are monitored in near-real time.
- Ensure alerts from security tools on Windows-based or Linux-based end-user systems on the OT network are transferred to the IT network in near-real time.
Although reasonable efforts will be made to ensure the completeness and accuracy of the information contained in our blog posts, no liability can be accepted by IANS or our Faculty members for the results of any actions taken by individuals or firms in connection with such information, opinions, or advice.