
Understand the Roles of Red, Blue and Purple Teams
Cyberattacks have become more profitable and attackers keep upping their game with advanced skills targeting businesses both large and small. To better respond to this ongoing barrage of attacks, organizations should continually look to improve their security posture.
By deploying red, blue and purple teams in exercises that identify weaknesses and defend against attacks, organizations can prepare themselves for the unavoidable “when,” not “if” attacks occur.
This piece takes a deeper dive into these teams to differentiate roles during exercises and help bolster both your cybersecurity offense and defense.
Roles of Red, Blue and Purple Teams
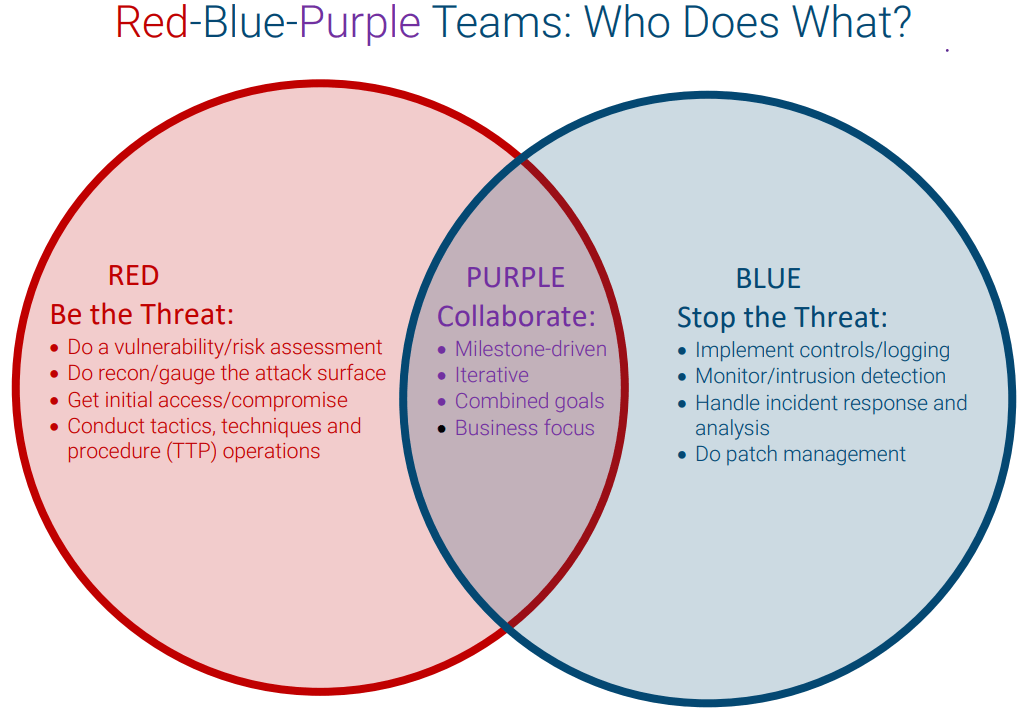
Traditionally, organizations have deployed red and blue teams in exercises, with red teams simulating security breaches and attacks, and blue teams defending against them. Each team plays a specific role during the exercise to help uncover security gaps and find ways to close them from both an offensive and defensive perspective. A purple team takes a different approach, serving as a collaborative effort and employing combined roles with an iterative strategy.
Understanding the roles of these three teams can help your organization protect and strengthen itself, and it can be extremely useful in validating the efficacy of your comprehensive security program.
Red Team Role: Be the Threat
The red team takes on the offensive role in typical exercises. To start, it performs initial reconnaissance to identify any vulnerabilities and risks, and then plans its methods of attack once it finds weaknesses to exploit. As a part of the exercise, the red team uses a variety of strategies, including but not limited to:
- Performing penetration testing to identify specific weaknesses
- Launching phishing, social engineering and other credential theft attacks
- Doing port scans
- Running vulnerability scans
Once the red team finds a window of opportunity, it determines the best tactics, techniques and procedures (TTPs) to use to exploit it. This includes infiltrating systems or exploiting physical perimeters while striving to avoid detection by blue team members. These exercises help provide a good indicator of the reliability of the blue team’s defensive abilities.
Blue Team Role: Stop the Threat
As the counterpart to the red team, the blue team focuses on defense. Its job is to detect, face off with and weaken the attacker (red team). The blue team closely monitors current and emerging threats, while preparing to provide a strong defense to protect its systems. Blue team objectives and tasks include:
- Finding suspicious traffic patterns on networks, systems and devices
- Searching for vulnerable areas and quickly responding to compromises
- Identifying red team attacks and blocking access
- Conducting internal and/or external vulnerability scans
- Collecting network traffic and forensic data to perform analysis and testing
- Understanding incident phases and how to respond appropriately
Essentially, the blue team is tasked with stopping threats through implementing controls, monitoring and detecting intrusions, handling response and analysis, and doing patch management. Other general tasks include doing DNS audits, risk assessments, managing firewall rules, performing reverse engineering on cyberattacks, and developing response and remediation policies to strengthen cybersecurity.
READ: Threat Hunting 101: Understand the Basics
Purple Team Role: Collaborate
A purple team is rooted in a collaborative philosophy to help red and blue teams gain insight into both offense and defense. The purple team methodology is business-focused and milestone-driven, helping both teams leverage their strengths to resolve any cybersecurity challenges they face. With a results-driven approach, purple teams:
- Identify gaps in training
- Test any previously untested TTPs
- Help teams acquire new security skills in real time
- Improve threat detection and response times
- Prioritize new risks to help minimize them earlier
- Provide recommendations to improve current security posture
- Analyze results and oversee remediation solutions
- Build a better security program
A purple team is not a long-term entity. It’s a transient team that helps encourage healthy competition while promoting cooperation and information-sharing to empower red and blue team members to think outside the box. Unlike typical red vs. blue team exercises, purple teams seek to capitalize on the strength of both teams to enhance everyone’s security knowledge and encourage knowledge transfer.
READ: Best Practices for Building Effective Purple Team Exercises
Team-Driven Exercises to Strengthen Security
Through consistent assessments, all red, blue and purple team members gain critical insight, helping the security team as a whole align goals and understand shared objectives. Overall, the combined team’s strengths will improve your organization’s security posture. All three teams serve a purposeful role in the quest for better cybersecurity. This includes helping to optimize cloud configurations, detecting internal and external vulnerabilities, and assisting in evaluating security service providers.
Organized red, blue and purple team exercises can prove to be highly effective for injecting stronger vulnerability detection into your cybersecurity plan, streamlining security improvements and increasing performance—without increasing your budget.
Together, these three teams can collaboratively overcome silos in an organization’s cybersecurity plan and form a stronger, more powerful, protective strategy against threat actors.
Although reasonable efforts will be made to ensure the completeness and accuracy of the information contained in our blog posts, no liability can be accepted by IANS or our Faculty members for the results of any actions taken by individuals or firms in connection with such information, opinions, or advice.