
Secure Both IT and OT Environments Effectively
Ensuring enterprise IT and OT are managed effectively and securely is no simple feat. This piece explains the primary IT and OT technology and staffing challenges and recommends some best practices for overcoming them.
OT Network Risks
With ransomware, every company is a target, but those managing both IT and OT devices represent a larger risk profile. When OT is added to the mix, more than just data is at risk: The company’s operations can come to a standstill. Even a partial loss of visibility can cause a shutdown of a manufacturing line due to quality or safety issues.
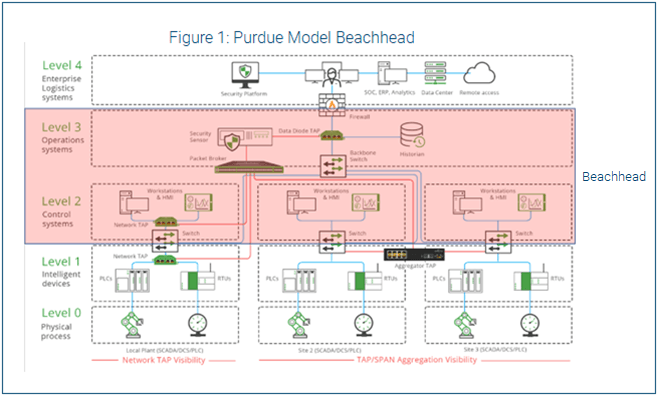
The most common way hackers compromise OT networks is to start with the IT network and move laterally to the OT side. Their first target on the OT side—what we call the “beachhead”—usually consists of higher-level OT systems, such as the human-machine interface, surveillance and information sharing, distributed control systems, etc. They typically run older-generation (unsupported) Windows and Linux and have access and control built in for entire segments of OT devices.
IT and OT Cultural Challenges
The starting point for combining IT and OT security management is to take a hard look at culture: The divide between IT and OT is more than just the proverbial airgap. The two teams differ in terms of:
- Technical background: Most OT operators start within a function or maintenance vs. security, and OT devices often use proprietary protocols IT personnel are unfamiliar with.
- Responsibilities: In security, the confidentiality, integrity and availability of data are paramount. In OT, high availability and safety are the top priorities.
- Concern about the risk: While security is focused on identifying and mitigating threats, many plant engineers are not even aware of the threats.
- Vocabulary: The same terminology can often have different meanings for IT vs. OT.
The technical foundation of security is asset visibility: What do I have, where do I have it and what is its current state? Consequently, many organizations charged with managing both IT and OT have implemented asset visibility tools with hybrid discovery
methods (primarily passive and some level of active scanning). They then work to extend that visibility to network traffic in an actionable manner.
Choose an OT Framework
The Purdue Enterprise Reference Architecture (the Purdue Model) is the most commonly used framework for designing OT networks, and it is based primarily on segmentation
and zoning. The beachhead, described earlier, represents Levels 2–3 of the Purdue Model. Proper segmentation supports operations, while ensuring risk reduction of impact and access. This segmentation needs to be done carefully because it can
often increase license and maintenance costs and, if done improperly, can negatively affect core operations.
However, Purdue doesn’t provide much insight into combining IT and OT security practices. The NIST Cyber Security Framework is the recommended framework.
READ: Industrial Control System (ICS) Risk Mitigation Checklist
Other frameworks to consider include:
- ISA/IEC 62443 is a cybersecurity framework that has gained momentum with ICS product manufacturers for certifying their devices for market.
- ISO/IEC 27001 is an enterprise IT certification standard useful for understanding security business processes, but it was designed for enterprise IT. It overlaps with
the IT Infrastructure Library but is more prescriptive as a certification vs. a general service management framework.
Structuring the IT/OT Organization
One option for structuring the IT/OT organization is setting up separate, dedicated teams for IT and OT infrastructure, because the requirements and skill sets are different. However, you should colocate both team’s personnel and data (OT equipment should still be segmented/isolated) as much as possible for team building and shared analysis. Because the IT environment is the most common initial access vector, the opportunities for detection begin there and can more easily be correlated with anomalous OT activity.
It's also important to conduct joint exercises as a team for training and education, including:
- Tabletops: Walk through scenarios together. Ransomware, incident response and an OT safety/availability issue are good foundational exercises.
- Purple teaming: Conducting a test on a production environment requires trust and technical skill. Start building trust by inviting OT personnel to join an IT-only purple team exercise and work toward scoping OT. Some variables to adjust include:
- Scope: Where the exercise happens
- Complexity: How detailed the technical execution is
- Frequency: How often you conduct exercises
Combined IT/OT Team Disadvantages
Once OT environments started increasing the number of IT technologies they used, many utilities started trying to identify ways to merge IT teams for both enterprise and OT environments. However, the downsides to this approach quickly became clear:
- IT best practices don’t always translate to OT: Many early efforts started taking IT best practices and implementing them in OT environments. While many IT best practices can work in OT, not all of them (e.g., quick patching) are recommended or even safe.
- Flatter networks spread malware more easily: This merging led to a flattening of networks and defenses. Consequently, malware in the enterprise started to spread to OT systems more easily, affecting processes. In addition, more advanced attackers were able to compromise network admin credentials and disable network defenses placed between the enterprise and OT environments, making compromises even easier.
- IT has trouble understanding OT if it isn’t always immersed in it: Traditional IT employees struggle to understand why OT environments are different, and if they only handle occasional work tickets from OT, they never get the opportunity
to fully understand the environment.
Some organizations that started down this merged path eventually changed directions and are now identifying ways to dedicate IT resources for OT environments.
IT/OT Reporting Structures
From a reporting structure, it doesn’t usually matter if that dedicated IT team reports through IT management or OT management. The most effective aspect seems to be putting the dedicated resources in place.
OT Security Best Practices
Managing both IT and OT securely is challenging. To ensure you create an environment for success:
- Don’t carry laptops that perform control operations outside the plant: Engineers shouldn’t be carrying such laptops to and from the facility, but instead, there should be a secure way for them to remotely access the laptop, when necessary. This is, of course, different for supervisory control and data acquisition environments, where a single engineer is responsible for many sites.
- Use a demilitarized zone (DMZ) between the business and control networks (as noted in the Purdue Model): This is different from your normal internet DMZ. Try to push all data from one side (control or business) to a server or service in the DMZ, and then have the other side pull that data from that server or service. This setup allows staffers to have a single point where they can limit traffic, inspect it and monitor it.
- Deploy a separate AD domain for OT: If AD is needed in an OT network, deploy a separate AD domain with no trust relations to the enterprise zone.
- Avoid sharing switching fabric between business and control networks, where possible: Try to manage all switches, routers and firewalls from the management interface in the control networks or via an out-of-band management network unique to the
control network and not shared with the enterprise.
From an architectural perspective, organizations should be trying to protect their OT environments from the enterprise in much the same way they protect the enterprise network from trusted business partners. Organizations don’t share VLANs and AD
domains with their business partners, but instead, find secure ways to pass required data safely between the two organizations, while maintaining some level of mutual distrust. That is a good mindset to have when designing defenses in industrial control
systems.
Although reasonable efforts will be made to ensure the completeness and accuracy of the information contained in our blog posts, no liability can be accepted by IANS or our Faculty members for the results of any actions taken by individuals or firms in
connection with such information, opinions, or advice.