
Best Practices to Detect & Prevent BEC Attacks
Business email compromise (BEC) attacks happen when someone uses email to pose as a legitimate, trusted source to commit fraud, for example, by submitting fictitious invoices for payment after changing the bank account number for a supplier. Some of the most common and damaging examples include fake invoicing, fraudulent routing number change requests and fake payment requests from executives.
The best ways to prevent/mitigate such attacks include requiring verification through external channels; implementing new, more stringent verification processes; educating users to recognize specific red flags (e.g., unusual, or extremely urgent requests); and deploying digital signatures for email.
This piece provides an overview of BEC attack methods and best practices to help detect and prevent this type of email fraud and spoofing.
BEC Attacks, Red Flags and Mitigations
There is a growing, wide variety of specific phishing attacks targeting all industry sectors in business. A BEC attack is a form of social engineering and a subset of spear-phishing.
Some of the most common and damaging BEC attacks include fake invoicing, routing number change requests and fake payment requests from executives.
Fake Invoicing
Fake invoicing happens when phishers pose as an existing vendor or supplier and send requests for payment of invoices to accounts payable.
- What to look for: Any requests to pay invoices that are unexpected, look unusual or request payment to a new account or location that is not anticipated.
- What to educate users on: Check the email address of the sender. We also recommend actually phoning the vendor or requestor using contact information NOT in the email (consult existing directories or information that is offline if possible). For any and all invoice requests, consult with two or three others within the organization who may be knowledgeable about the vendor and expected payments to validate the request.
READ: 10 Ways to Identify a Phishing Email
Routing Number Change Requests
Similar to the invoicing example, this happens when a supplier or vendor requests a routing number change. This potentially has more impact than the invoicing example because it’s more “permanent.”
- What to look for: Any requests to change a routing number that are unexpected, look unusual or request payment to a new account or location that is not anticipated.
- What to educate users on: Check the email address of the sender. We also recommend actually phoning the vendor or requestor using contact information NOT in the email (consult existing directories or information that is offline if possible). For any and all routing number requests, consult with two or three others within the organization who may be knowledgeable about the vendor and expected payments to validate the request.
Fake Payment Requests from Executives
A common phishing scam is to impersonate a trusted executive with authority to request financial transfer of funds (see Figure 1). The request could be for a variety of reasons, including vendor/supplier payments, new projects, bonus pool fund allocation, expense reimbursements, stock or other trusts, etc.
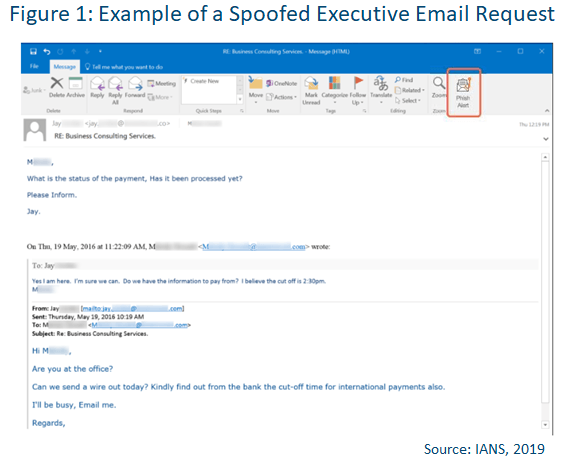
- What to look for: Any requests from top executives to move or channel funds somewhere should be immediately suspect, even if they come from the chief financial officer (CFO). Look for unusual use of language or cadence, or sense of urgency implications. In particular, wire transfer requests should be immediately suspect. Also, attempts to intimidate junior or new employees should be red flags.
- What to educate users on: Check the email address of the sender, and we recommend actually phoning the executive or visiting them in person to confirm the request. No funds transfer should be performed without multiple parties confirming definitively the request is legitimate.
How to Mitigate BEC Attacks
Consider using the following best practices to help mitigate BEC attacks.
- Require verification through external channels. Employees should reach out through other official channels, such as using known phone numbers from the company’s phone directory to call the person directly, contacting their assistant or even just walking down the hall to speak with the alleged requester face to face. These simple steps can mitigate many of these attacks.
- Implement new verification processes. Putting the right account verification and safeguard processes in place can derail these phishing attempts. This could entail requiring employees to follow set processes (such as performing account verification, requiring secondary and/or tertiary signatures by other personnel, and requiring phone verification, etc.) before making any transfers over a set amount — for example, $10,000.
- Educate users on specific red flags, such as:
- Any change in invoicing or routing number.
- Sense of urgency.
- Direct requests from executives that are unusual or intimidating.
- Requests from new vendors or suppliers.
- Payment requests that do not copy multiple parties in finance and accounting.
- Forwarded requests for assistance due to “someone else not helping.” This is very common.
- Look to implement digital signatures for emails. While implementing email validation and verification can take time and cost some additional money, it’s critical to help in validating senders, especially those from within the same organization.
READ: How to Create an Effective Anti-Phishing Program
BEC attacks are easy to fall for and hard to detect but there will usually be red flag indicators to help mitigate attacks. Performing regular security risk assessments and keeping both anti-phishing tools along with risk mitigation plans updated helps to build effective anti-BEC programs. Individuals are the vulnerable link in BEC attacks, and organizations should offer consistent education, training and simulations to help employees recognize and report potential BEC attacks.
Although reasonable efforts will be made to ensure the completeness and accuracy of the information contained in our blog posts, no liability can be accepted by IANS or our Faculty members for the results of any actions taken by individuals or firms in connection with such information, opinions, or advice.