
The Importance of Supplier Continuity Exercises
Central to a supplier risk management program is understanding, measuring and managing the level of risk exposure in the relationship between the supplier and enterprise from a resiliency and continuity perspective. To achieve this, enterprises should identify their most critical suppliers and then verify their continuity capabilities. This piece explains how this verification process must go beyond supplier security reviews to include an independent validation of the supplier’s continuity plans, combined with ongoing exercises to ensure the enterprise and supplier resilience efforts are coordinated effectively.
Planning Supplier Continuity Exercises
Many organizations identify key high-risk suppliers to conduct periodic exercises to test their business continuity (BC) best practice plans (something that must be agreed on by contract). Figure 1 below provides a framework that can help support the execution of supplier continuity exercises. It is organized by plan objective, purpose and scope, and the components of the plan cover BC, cybersecurity implications and communications.
Organizations should consider developing and deploying detailed procedures across the enterprise in support of each of these plans.
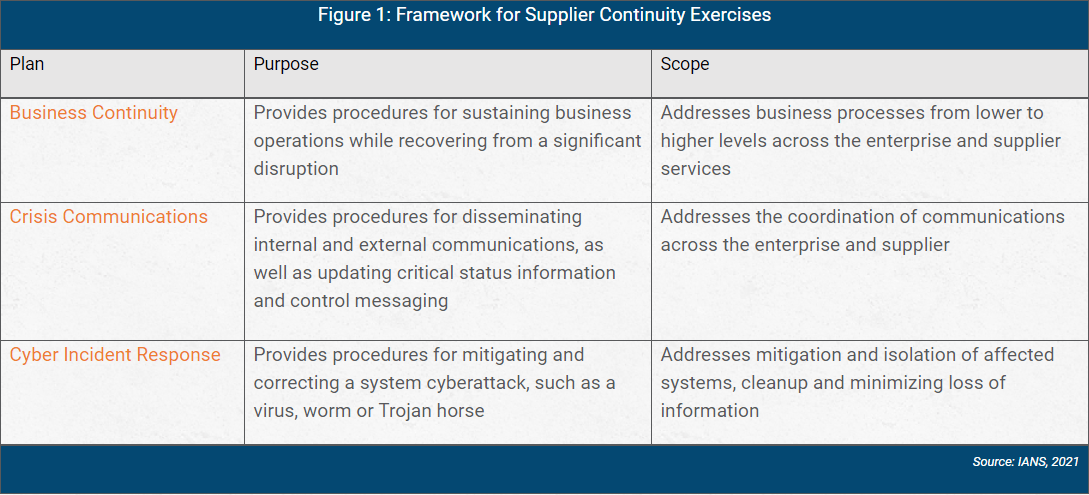
Once procedures are defined and documented, enterprises should conduct exercises with suppliers according to their criticality to the enterprise and its core business operations.
Factors to be considered include:
- Types of data accessed and processed by the supplier.
- Impact on service availability if there is a disruption.
- Any regulatory/compliance implications.
Setting Up Supplier Tabletops
Successful supplier tabletops require strong processes and upfront planning. Key preliminary steps to take include:
- Identify participants. It is incumbent on the enterprise to identify business representatives (supplier relationship owners) to participate in exercises with the supplier. Participants should include information security, sourcing, business representatives, BC teams and technology.
- Create impact assessments. These are central to the supplier risk assessment process and should be created prior to engaging the supplier. An impact assessment should be aligned to the following cyber-attack categories: business interruption, fraud, intellectual property (IP) theft and loss of customer data.
- Obtain supplier buy-in. The supplier should have complete agreement and cooperation to participate in the exercise. These terms, including points of contact, should be stated in the contract.
Running Effective Supplier Tabletops
Running supplier tabletops is a lot like running internal tabletops. The main differences are the external coordination with the supplier and touchpoints with internal resources. Consider these key steps:
- Use cyber scenarios that represent material exposure to the business. An example could be centered around a ransomware attack disrupting a major portion of the business while siphoning data from the network. The supplier could be compromised and serve as conduit for the attackers to enter the network.
- Document the exercise. It is critical to ensure notes are taken that include observations and corrective actions. Both the company and supplier should document the exercise.
- Document lessons learned. Lessons learned can apply to both the supplier and enterprise and should be tracked by information security and the sourcing organization until remediation.
- Measure improvement. Metrics should be deployed that measure improvement over time. For example, time to response and recovery can be key metrics for measuring success.
Supplier Contract Language Considerations
The contract should embed language that articulates the supplier’s participation in the ongoing exercises and addresses material areas of exposure. Consider using the following sample contract language:
- Supplier shall maintain a comprehensive business continuity plan that is commercially reasonable and complies with applicable law, rules and regulations.
- The supplier will provide an executive summary of such plan on reasonable request.
- The supplier will test the adequacy of its business continuity plan in a coordinated exercise with the company at least annually.
- In the event of business disruption that materially impacts supplier provision of service under this agreement, supplier will notify the company of the disruption and the steps being taken in response.
Supplier Continuity Exercise Services
A wide range of services and consultants can assist in the coordination of supplier/enterprise exercises. Any provider you choose should offer a discussion-based incident scenario tailored to your unique environment and operational needs. When selecting a provider, consider:
- Customization. The exercise should be based on you and your supplier’s environment, including specific applications, controls and processes relevant to your business. A scenario should be developed that is both relevant to the threat landscape and specific to your high-value assets and processes.
- Accuracy. The exercise should guide your organization through the scenario that accurately mimics a targeted event.
- Real-world inputs. Realism is the key to effectiveness, so the exercise should features injects that simulate real-world inputs. This will test you and your supplier’s ability to respond to new information as it occurs while probing your investigation, communication, coordination and recover capabilities.
It is critical to ensure the scenarios provided are relevant to your internal business processes and the supplier’s services. Moreover, contract language should state an agreed-on cadence of exercises and the necessity of addressing material findings.
Supplier Business Continuity (BC) Exercise Tips
Organizations can’t properly manage supplier risk unless they understand, measure and proactively manage the level of risk exposure from a resiliency and continuity perspective. To be successful with supplier BC exercises:
- Identify your most critical suppliers and get them on board with exercises via appropriate contract language.
- Get the right people and processes in place, and include plans across BC, communications and incident response.
- Test using real-world scenarios, and consider hiring a firm to develop and coordinate the exercises.
- Learn and iterate. Ensure exercises and lessons learned are fully documented, and that issues are remediated in a timely manner. Continuously test the effectiveness of the program to drive the level of resilience maturity.
Although reasonable efforts will be made to ensure the completeness and accuracy of the information contained in our blog posts, no liability can be accepted by IANS or our Faculty members for the results of any actions taken by individuals or firms in
connection with such information, opinions, or advice.