
Top AppSec Training Resources
In a rapidly changing space, it is critical for application security professionals (AppSec) to stay sharp and keep up with development trends. Partnering with security reliability engineers (SREs) and development architecture teams to gain deep insight into what is happening within the organization as well as within the technical community should be a part of this. This is in addition to other key learnings that can be sourced from internal architecture diagrams.
Application security conferences do not always cover the right platforms, languages, etc., while developer conferences can sometimes be too deep and time intensive. This piece provides ways AppSec professionals can keep up with emerging technologies in the development world with resources focused on broad knowledge and models for continuing education to learn more about development process and tools.
SRE Team
This is a big space. With the software development lifecycle (SDLC) and the ever-changing components of the continuous integration/continuous delivery (CI/CD) pipeline, you need to understand it all to create a security pipeline that gives you visibility and guardrails baked into the engineering process.
Your SRE team can be a great resource. For example, if your organization is deciding to use Kubernetes and Docker containers in your Amazon Web Services (AWS) staging environments, you could partner with the SRE team and get a vulnerability scanning tool for the stack. In doing so, the SRE team can give you a heads up about the container environment and do the research to look for new tooling. From here, try and determine your top picks, and then lean on the SRE team to select the solution, even though it would likely come out of your budget.
Consider the SRE team as an extension of information security, since it is responsible for the availability part of information security’s confidentiality, integrity and availability (CIA) triad. SREs are seasoned professionals who should have a good understanding of application security and are highly motivated to reduce the cost and outages caused by bug fixes and patches for code deployments.
Architecture Diagrams
Architecture diagrams and data flows also can be useful for identifying what projects, applications and services are being used by development and other lines of business. These surface up all kinds of rogue or shadow IT applications that are not properly being secured.
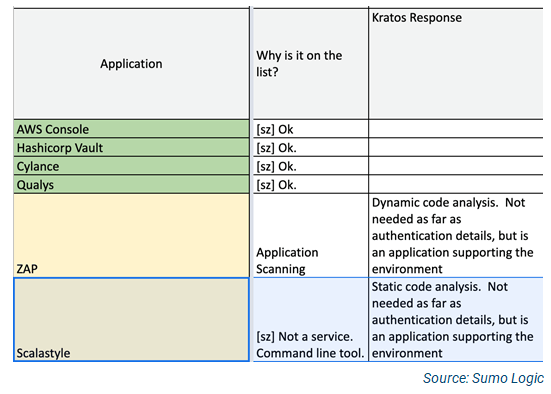
How did this team get this done? They used spreadsheet as a working collaboration document with the developers and auditor to identify apps vs. controls (see Figure 1). ZAP and Scalastyle at the end of the list are application scanning tools.
Figure 1: Spreadsheet Shows Applications vs. Controls
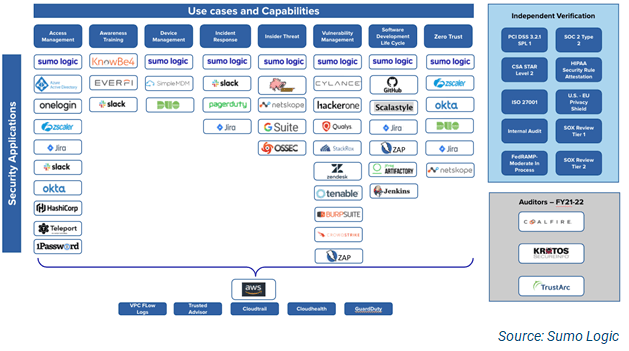
This led to the eventual build out of a security application matrix to support the SDLC and CI/CD pipeline efforts to expose potential gaps as shown in the Figure 2 in our example case. Notice the use case under SDLC lists out some of the tools we use in our security pipeline.
Figure 2: Example of a Security Applications
Recommended AppSec Conferences
Too often, the largest security conferences lack the depth and breadth of information AppSec professionals need. Options like BSides and DEF CON are still viable, they can be too costly for smaller information security teams with limited budgets.
Consider attending the big cloud service provider (CSP) conferences, like AWS Re:Invent, Microsoft Ignite and Google Cloud Summit.
Also consider HackerOne, Bugcrowd and Contrast as these conferences often have full blown AppSec tracks, plus, they are virtual through 2021 and free for the most part. This provides AppSec professionals the flexibility to pick and choose what courses to attend, while keeping your costs minimal.
AppSec Training & Continued Education
It can be challenging for AppSec teams to stay up-to-date on the latest development strategies and technologies. To keep on top of things:
Collaborate and partner with your SRE and development architecture teams. This is crucial. They should know what is currently being used and what is coming in the future. Their roadmaps are great resources, and they care about regulatory requirements and reducing costs. The last thing they want is a disruption after applications go into production. In fact, most SREs and developers have management by objectives (MBOs) on availability.
Consider moving toward more of a DevSecOps model. Not only will you gain business benefits, but you will also be able to better integrate security into the development process.
Although reasonable efforts will be made to ensure the completeness and accuracy of the information contained in our blog posts, no liability can be accepted by IANS or our Faculty members for the results of any actions taken by individuals or firms in connection with such information, opinions, or advice.