
InfoSec Project Management Best Practices
Implementing complex security technology is difficult enough, without throwing multiple IT teams and business stakeholders in the mix. Often security teams are looking for improved workflows and project prioritization while being cognizant of implementing processes and procedures that will not be seen as negatively impacting other areas. This piece outlines InfoSec project management best practices.
Keys to InfoSec Project Management
Problems with projects coming in on time, on budget and within specifications are common in all functions of business. Technology projects, either in IT or information security, are no different, but come with their own set of complications. While the technology to be implemented does play a role in the outcome of a project, the main determinants of success are closely tied to process and leadership.
Many times, staff try to drive enterprise projects that change the way people work and cause disruptions in workflows. These activities are rarely successful when driven from the bottom up by technology experts. Instead, security staffers and project planners should try to interact and communicate early with all affected parties so they can gain cooperation from the majority and then use the governance structure to encourage the few who are non-compliant.
A common mistake with technology projects is having the line staff be the same experts who are assigned both critical technology work and critical project work. Project management is a separate set of skills and needs to have appropriate resourcing. To be successful, a governance structure should be put in place with leadership from all affected areas and from institutional leadership. By using some basic processes, assigning clear accountability for success, and being assertive with visibility and transparency of the work status and barriers, the team can greatly improve its chances for better outcomes.
Step 1: Get Oversight in Place
Technology projects are full of risks and challenges, but the outcomes you should consider aiming for are either a successful project or one where deficits are visible, transparent, understood and approved by the project sponsors and the institution. To have this kind of environment, there must be engaged governance and oversight. This should include an institutional security committee that assists with defining priorities and has leadership from across the business areas. We recommend this group holding regular meetings, be involved in project prioritization and having regular work status reports.
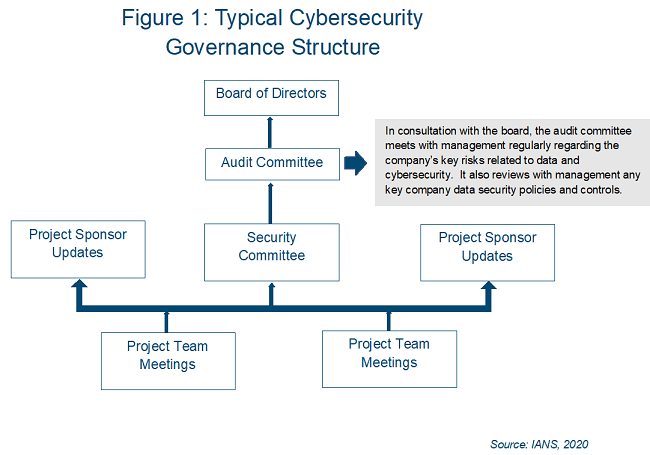
Consider providing the security committee with access to the audit committee for regular updates, as well as regular reporting to the board of directors. Figure 1 provides an example of a typical governance structure, including the role of the audit committee.
Step 2: Project Management Processes
Project management processes are also critical for success. The outcome of these processes are to:
- Make sure you have identified stakeholders and leadership.
- Have clear assignments and accountability.
- Involve all participants during requirements and design.
- Objectively communicate status and barriers.
Many tools are available from multiple sources to help in the documentation of a project, but an important thing to remember is that the documentation is an outcome of doing the work and not an end. High-priority processes that should be put in place include:
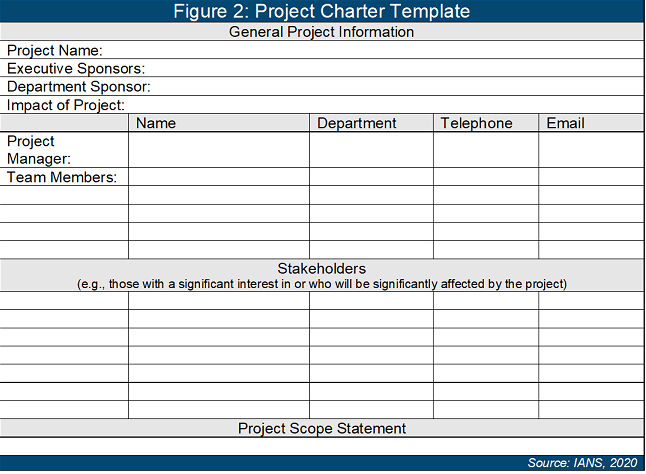
- Project charters, with identified sponsors, accountable individuals, timelines and resources (see Figure 2).
- A project plan, listing tasks at a medium level of granularity with responsible individuals.
- A design and planning phase, paying additional attention to groups that may be resistant.
- Reporting and metrics, to drive visibility to leadership in case additional influence is needed.
Consider flow-charting affected workflows to be able to clearly articulate the changes that need to be made early during the design and planning phase. This includes both new activities for staff, as well ones no longer needed.
Step 3: Communicate/Manage Risk and Status
A third task is to manage and communicate the risks and status of a project. This means identifying anticipated risks as well as having a risk log that is regularly reviewed.
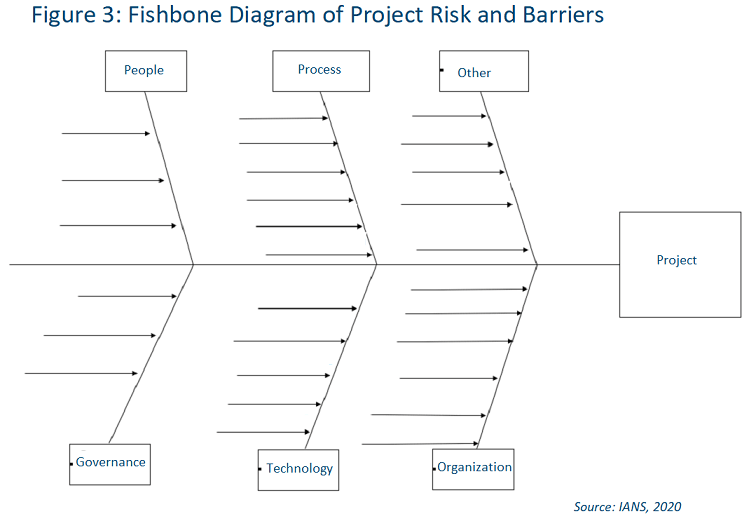
Initial risks can be collected using a fishbone diagram (see Figure 3).
Then, ongoing risks can be added to a risk log.
Risks, barriers and project status should also be entered into a dashboard and presented to leadership with plans to overcome them, along with details about any assistance needed. If you are unable to overcome the barriers and leadership is unwilling to assist, this needs to be documented and appropriate updates made to whatever project aspects are affected.
Step 4: Develop a Project Plan
The fourth critical step is to develop a project plan that lists the task, timelines and resources, and identifies dependencies. In IT, it can be very easy to overdo a project plan, making it difficult to maintain and understand. The plan can be done using multiple tools, ranging from enterprise project planning (EPM) software to a low-tech whiteboard approach. The only rule is the tool and details must match both the organization’s maturity and the complexity of the work.
No matter the tool or format, it is important to be able to track accountable resources and impacts of barriers or delays. It is also beneficial if a larger multi-year plan is broken down into “edible” six months of detail so individual tasks are better understood.
InfoSec Technology Implementation Tips
To sum up, successful implementation of security technology across departments requires:
- Having appropriate governance and leadership accountability in place.
- Using best practice project management principles tailored to the skills and complexity of the project leaders and the work.
- Involving all stakeholders early in the process and clearly communicating deliverables and accountability.
- Making the project status, including barriers and delays, visible and transparent to sponsors and leadership committees.
However, it’s also important during all the planning and communication, you are able to articulate the outcome as meeting a business need. For example, try to avoid naming your project “Implement NAC,” rather consider a name such as “Decrease the Risk of a Sensitive Data Breach.” This allows you to better communicate to teams outside of security and to leadership the impacts of delays and inability to meet requirements. As you provide status reports to the project sponsors and leadership, it also allows you to frame the discussion and potential impacts in terms they understand.
Although reasonable efforts will be made to ensure the completeness and accuracy of the information contained in our blog posts, no liability can be accepted by IANS or our Faculty members for the results of any actions taken by individuals or firms in connection with such information, opinions, or advice.