
Getting Started With SOC & SOAR Automation
Security orchestration, automation, and response (SOAR) platforms have become a reality for offloading well-defined tasks within the security operations center (SOC). However, deploying a SOAR tool successfully requires careful planning around technology integrations, use cases and key performance indicators (KPIs). We recommend starting small and going for quick wins initially, adding on more use cases and integrations as your familiarity with the platform improves.
In this piece, we provide guidance on how to get the most from automation within your security operations center (SOC).
SOAR Automation Challenges
Automation, and specifically SOAR, can present challenges to security teams, including:
- Managing integrations to the plethora of products that may be needed to effectively deliver automation, especially the SIEM.
- Defining use cases that will solve large problems, but not hurt the organization. If you automate the wrong things, there is a potential to cause damage at scale.
- Measuring success. If you team starts with too many use cases and integrations, there is a chance you could find it difficult to measure them all effectively.
At a high level, most of this can be avoided by:
- Integrating automation into your SIEM solution.
- Defining simple use cases. Identify simple, repeatable tasks and automate them.
- Setting proper KPIs for the SOC. Consider focusing on the severity of incidents and how you respond (mean time to repair, etc.).
- Identifying or hiring talent to build playbooks and maintain them. You will also need folks with Python and scripting skills to help with tool integrations.
SOAR Automation: Getting Started
Finding use cases and quick wins might be the most difficult task. The trick is to start small. For example, consider building your new SOAR platform around these three use cases:
Endpoint attacks: Have the SOAR platform ingest threat feed data from endpoint detection tools such as Cylance, Carbon Black, CrowdStrike, etc., and then run queries for machines and endpoint names with malicious indicators. The SOAR platform could then cross-reference retrieved files and hashes with SIEM data and verify whether any indicators were picked up and resolved by SIEM actions. The SOAR platform can also notify analysts if SIEM actions have already resolved any malicious indicators.
Failed user logins: When the number of failed logins on an end-user device exceeds the allowed maximum, the SOAR platform could automatically inform the affected user and ask them to confirm whether they made the attempts. If the user says yes, the SOAR platform can reset the password and send a new email to the affected user with revised login credentials. If the user says no, the SOAR platform can send a new email notifying them of the account takeover attempt. The SOAR platform can also execute investigative actions, such as extracting the IP and location where the failed attempts were made from and quarantining the affected endpoint.
Phishing attacks: Alerts to suspected phishing emails come from a variety of detection sources, such as SIEMs and logging services, as well as end users who forward emails that look like they contain malicious content. The SOAR platform can aggregate the suspected phishing emails and automatically trigger a process to inform affected end users about potential malicious emails being investigated. As part of the triage process, the SOAR platform can extract compromised indicators. By looking at the header and content of the email – including the subject, email address and attachments – the SOAR platform can assign an incident severity value and check for reputation red flags by cross-referencing the data against external threat intelligence databases. If any malicious indicators are found, the SOAR platform can inform affected users and provide instructions on what to do. The SOAR platform can also scan all email accounts and endpoints to identify other instances of the malicious email and delete them. The SOAR platform can then add the malicious indicators to blacklists tracked by other security tools.
Defining SOC KPIs
Defining clear KPIs is also important. When automating the SOC, KPIs should focus on the severity of incidents and how you respond, including mean time to repair, communication, establishing guard rails to prevent the incidents from happening again, and post-mortems.
Figure 1 shows an executive-level report of SOC KPIs where automation is needed to accomplish a good portion of the actions.
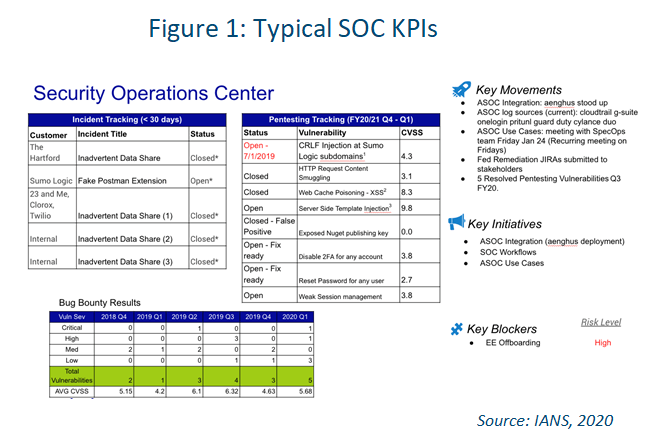
As you build out your integrations and use cases, it’s also important to test everything carefully. Consider setting everything up first in a sandbox environment, so you can be sure nothing breaks when you kick off the automation.
SOAR Automation Tips
- Integrate your SOAR solution with your SIEM first.
- Pick a simple use case to start and execute it into production.
- Measure results carefully.
A quick win can help get you off to a solid start - again, consider the idea of endpoint attacks or phishing. Both have a lot of visibility and will help you drive more resources and projects from an executive level. You will need resources with Python
and scripting skills that report to or support the SOC. They can lay out the framework and then hand over the results to an analyst.
Although reasonable efforts will be made to ensure the completeness and accuracy of the information contained in our blog posts, no liability can be accepted by IANS or our Faculty members for the results of any actions taken by individuals or firms in connection with such information, opinions, or advice.