
Cloud Application Security Best Practices
A move to the cloud requires an initial focus on information security training and governance, including understanding the shared responsibility model and key differences in tooling for traditional on-prem vs. cloud environments. From there, it’s a matter of choosing the right cloud service provider (CSP) and establishing a critical set of CSP services, third-party controls and traditional security best practices. In this piece we outline a series of steps to take to help ensure a solid cloud security foundation for your organization moving forward.
Cloud Security Foundation
Here are a few high-level considerations for InfoSec teams with respect to best practices when it comes to establishing a foundation for cloud security.
- What are the first 10-20 things you should do to secure the cloud?
- What controls are minimum requirements, and how do those change by cloud provider?
- What are the toughest aspects of basic cloud security, and how can you make them easier?
Cloud Security Training
Moving to the cloud can be overwhelming. Organizations that are quick to drive a cloud-first approach to try and cut costs and increase speed can sometimes fail to account for new tools, training and security best practices.
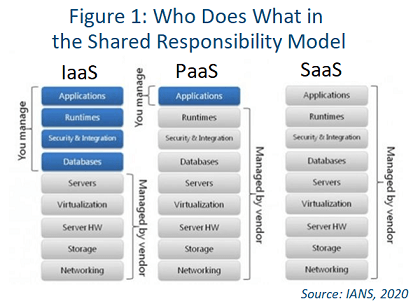
The best place to start is with training and understanding the shared responsibility model for infrastructure-, platform- and software-as-a-service (IaaS/PaaS/SaaS). These concepts (see Figure 1) are mostly cloud-agnostic, but there are some subtle differences between providers. Training does not have to be expensive. There are plenty of very effective, reasonably priced options, such those from Udemy and Cloud Academy.
Cloud-Centric Framework
Consider a cloud-centric framework to drive regulatory standards and audit success. Frameworks provide a selection of controls that should be implemented for cloud computing and security. For example, the NIST Cybersecurity Framework (CSF) is commonly used, even for those with no federal requirements.
Focus on IAM, SSO and MFA
Keep in mind that identity and access management (IAM) is largely up to you (not the cloud provider). It might be beneficial to start by trying to leverage cloud solutions for single sign-on (SSO) and multifactor authentication (MFA). These models allow you to focus on what really matters most: your applications and data. It is still prudent to get visibility throughout the entire stack, but focusing on SSO and MFA narrows the scope of what you manage.
Understand Differences in Tooling, Visibility
In an on-premises environment, you have rigorous rules for security and software deployments. You may only run vulnerability scans at certain times, and most security products are built to work “in line,” meaning on a network either as a proxy or spanning ports on a device.
In the cloud, however, the best practice is to do security at the host or virtual machine (VM) level. For example, most organizations load up all hosts with firewalls, intrusion detection systems (IDS) and other endpoint security solutions to capture information (i.e., logs) in real time from the source.
Unfortunately, on-prem security solutions do not always cut it in cloud. They are not built with modern API-based architectures, which makes data collection and integrations with CSPs extremely difficult, if not impossible.
Choosing a Cloud Service Provider
Another challenge is figuring out which cloud provider is best for you. When it comes to IaaS, three major players are: Amazon Web Services (AWS), Google Cloud Platform (GCP) and Microsoft Azure. They all have great security controls and services that help tremendously with visibility and logging, but they do have their differences, so be sure to examine each more closely.
Cloud Security Provider Must-Haves
A mix of CSP services, third-party tools and traditional security controls are all required for a secure move to the cloud. When it comes to CSP services, must-haves from CSPs include, but not limited to:
- Flow logs (e.g., VPC Flow Logs, Network Watcher)
- Audit logs (e.g., CloudTrail, Azure Audit logs)
- Encryption (e.g., AWS KMS, Azure Key Vault)
- Threat detection or advanced threat protection (e.g., ATP)
- Distributed denial-of-service (DDoS) protection (e.g., AWS Shield)
Consider using third parties to avoid CSP vendor lock-in and keep the portfolio open for a potential/eventual move to a multi-cloud environment. For example, your AWS WAF will not work on Azure or GCP. Third-party tool considerations, include:
- SSO
- MFA
- IDS
- Web application firewalls (WAFs)
- File integrity monitoring (FIM)
- Next-generation endpoint protection
- CASB (DLP)
- Cloud SIEM
Keep in mind, you also need to retain access to certain traditional controls, as per the shared responsibility model in Figure 1.
Set Up a Cloud Security Foundation
- Do not lift and shift. Start your cloud deployment with greenfield applications and workloads. Wait until you have to re-factor your legacy three-tiered applications.
- Do your homework. Learn the shared responsibility model and about any CSP services unique to its environment.
- Keep an eye to the future. Augment with third-party solutions that will allow you to pivot from CSP to CSP.
Although reasonable efforts will be made to ensure the completeness and accuracy of the information contained in our blog posts, no liability can be accepted by IANS or our Faculty members for the results of any actions taken by individuals or firms in connection with such information, opinions, or advice.